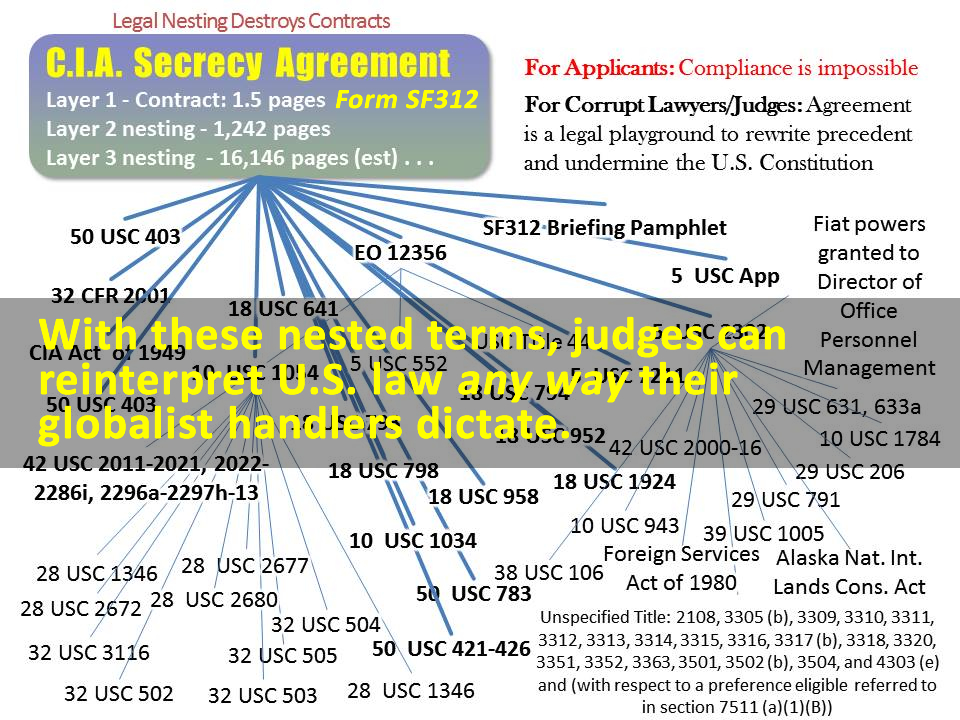
Pretext "false flags" like fabricated stories of genocide are used to discredit opposition, hide the truth and consolidate globalist power

Fig. 1: Bill Clinton, George Bush & Barack Obama colluded to give American sovereignty over to globalists who are committing sedition against the U.S. Constitutional and running an illegal, rogue C.I.A.
Photo: Media City Groove.
A Racketeer is someone who makes money from a pattern of illegal activities.
(Apr. 21, 2017)—President Bill Clinton labeled the tragic conflicts in Rwanda (1994) and Kosovo (1998) as genocidal rage. What are the odds of one U.S. president encountering not one but two "genocides" in very small countries within four years? What changed to trigger such sudden furor? Who paid for it? Who organized it? What was the end game?
With the benefit of hindsight, a rogue C.I.A. aligned with globalist corporations appears to have been the secret power fomenting these acts of violence. It appears that in classical spy misdirection, the over one million victims of Rwanda and Kosovo were made out to be the causes. This false narrative was supported by a complicit mainstream media.
On May 12, 2005 FBI Special Agent In Charge Ted L. Gunderson said "people in our government . . . a rogue outfit" inside the C.I.A. is behind all the acts of terror since Bill and Hillary Clinton came to power in 1993. (Editors' Note: Many links in this post, like this one, are bookmarks in a detailed TIMELINE and bibliography. Once clicked, please be patient for it to load and go automatically to the timeline entry)
Gunderson, a former station chief in Memphis, Dallas and Los Angeles and candidate for FBI Director in 1979, called them a "covert military criminal enterprise, government enterprise, primarily by US military intelligence, that is operating full throttle and everybody [in the FBI and Justice Department] refuses to investigate it."
Clinton's racketeering for Deep State globalism
In the two days before George Bush became President, Bill Clinton made some telling moves that can only be understood now.
Clinton pardoned his former C.I.A. spy chief John M. Deutch for mishandling classified information and likely much more. Deutch was C.I.A. director when it appears the scheme to form a Deep State shadow government global Internet-based surveillance system was hatched.
Notably, Deutch's daughter-in-law, Marne L. Levine, worked for Larry Summers as Treasury Secretary (1993-2001), Harvard (2002-2004), National Economic Council (2008), and now at Instagram (2014-current) where she is chief operating officer. Summers had popped up as Instagram's sole director just before Instagram sold to Facebook for $1 billion. Summers' former student, Gmail founder and chief of staff at the Treasury Department, Sheryl K. Sandberg, brokered the Instagram deal as Facebook chief operating officer. The collusion is evident. Summers and Sandberg were colleagues with Russian oligarchs Yuri Milner and Alisher Usmanov. Milner and Usmanov were also Goldman Sachs partners in Moscow.
These seemingly unconnected events now show, in hindsight, that the C.I.A., Google, Facebook and those with whom they collude have been part of a globalist takeover plan for decades. It certainly proves they planned long ago to control the Internet, email and social networking.
For the record, along with C.I.A. Deutch, Clinton also pardoned his fugitive financier buddy Marc Rich who was living in Switzerland to escape extradition to the US. for tax evasion.
Then, in a weird twist, Clinton appointed Microsoft’s CEO Bill Gates and his national security spy attorney, James P. Chandler, to the National Infrastructure Assurance/Advisory Council (NIAC). Why would the outgoing President take such a proactive step when the next president could easily cancel the order?
The theft of the social networking invention
At the time of his NIAC appointment, James P. Chandler was also the patent attorney for Columbus OH innovator Michael McKibben and Leader Technologies. Leader had engaged him in early 2000 to protect and patent their new invention: social networking. Chandler became a Leader director as well.
In the mid 1990's, McKibben had rebuilt AT&T's email system, AT&T Access Plus 3.0, in time for the launch of Windows 95 by Bill Gates. (Secretly, Gates & AT&T had temporarily fallen out on how Microsoft was going to control Internet email and browser protocols, opening the door for McKibben's team.)
McKibben then founded Leader Technologies to innovate an entirely new approach for Internet collaboration. McKibben had seen that legacy "groupware" software platforms offered by IBM, AT&T and Microsoft (i.e., Microsoft Exchange, Lotus Notes, Novel Groupwise and IBM Websphere) would fundamentally fail to scale to the transaction volume needed by the emerging Internet. In fact, McKibben and his team successfully revived and dramatically enhanced the AT&T Email system after the AT&T Lotus/IBM Network Notes and cc:Mail offerings failed to work as advertised. AT&T sales promotion (Nov. 28, 1995): "We've enhanced it so much it's out of this world."
Unknown to Leader, Chandler was already colluding with IBM, AT&T, Microsoft, the Clintons, C.I.A., NSA, FBI, Eric Holder, David Kappos, the Bushes, Larry Summers, Robert Mueller and John Podesta, among many, and stole Leader's invention to fix the technology shortcomings of their shadow government—in the name of "national security" of course. Leader's investors had risked over $10 million dollars and Leader's engineers had created over 750,000 lines of source code. This invention, stripped of its personal security and privacy programs, is the engine that drives the rogue CIA-controlled "social" Internet today in a diabolical public-private racketeering scheme of global proportions.
During this time, Mark Zuckerberg was a junior in high school. Zuckerberg's now well-recognized pathological lying would fit the profile needed by the C.I.A. MKUltra mind control program. Zuckerberg's all-too-perfect Harvard narrative was quickly promoted by Fortune magazine's David Kirkpatrick in The Facebook Effect, and Hollywood in The Social Network. The Zuckerberg phoenix-like Harvard dorm story emerged: (1) after Clintonista C.I.A. agent Larry Summers was appointed president of Harvard, (2) C.I.A. agent Marne L. Levine became his chief of staff, (3) Summers and Levine fended off four other competing Harvard facebooks (Ceglia, Winklevosses, Greenspan, Harvard admin) until Leader Technologies' invention was debugged (Oct. 28, 2003), and (4) the warrantless surveillance of Americans was initiated by Project Stellar Wind. In addition, certain unsolved New York "Craigslist killer" abductions and the disappearance of Jessica Taylor on Long Island keep coming into view given the shadow government's preference for using sex, drugs, pedophilia and murder to blackmail and control targets. What is known from sworn testimony is that Zuckerberg favored Craigslist for arranging dates and advertising his programming services back then. Craigslist is how he first met Paul Ceglia and others. See FBI Special Agent In Charge Ted L. Gunderson.
New, Apr. 25, 2017: Clearly, Congress, the Justice Department or local law enforcement in Long Island needs to impound Zuckerberg's 28 stonewalled computer devices from Harvard (2003-2004) before they are destroyed by his attorneys, McManis Faulkner LLP and Gibson Dunn LLP, who have had custody of them and have lied to and misled multiple federal and state courts about this important evidence. It might include instant message (AOL IM) discussions of poison ivy, unmarked burlap sacks, an apartment on top of a Chinese restaurant, a Ute car handy for hauling, or not. See also AFI. (Mar. 26, 2017). "House Intelligence Committee: Impound Zuckerberg's 28 computers and prove real Russian meddling."... Russians working with the Clintons long before the 2016 election.
1st Clue: Both Presidents Bush and Obama extended and enhanced the NIAC's powers with more than 23 additional executive orders. This became a technology platform that is parallel to the NSA's, but used without regard to the Constitution. This duplicity is confirmed by William Binney, the NSA's chief architect, pushed out on Oct. 31, 2001.
2nd Clue: This occurred just eight months before 9/11 and the Patriot Act. Remember, FBI Special Agent In Charge Ted L. Gunderson said 9/11 was a rogue C.I.A. false flag pretext designed to push the country into approving the Patriot Act that Gunderson said "takes away many of our constitutional rights and civil liberties."
Indeed, Clinton had formed NIAC by Executive Order 13130 on July 14, 1999. Nine weeks later on Sep. 29, 1999, Clinton ordered the C.I.A. to form a private venture capital company called In-Q-Tel. Two weeks later, on Nov. 12, 1999, Clinton and Summers abolished Glass-Steagall banking controls that ushered in the era of "too big to fail" banks, like Citigroup. Citibank then torched mortgage lending controls, thus making the 2008 crash inevitable. More collusion is evident.
The list of founding trustees for C.I.A. In-Q-Tel is telling. They are all prominent in the military-industrial complex that President Dwight D. Eisenhower warned about in his Jan. 17, 1961 farewell address:
Telecredit, Inc., Lockheed, Xerox, Columbia University, Goldman Sachs, Marsh & McLennan Capital, Inc.,
Technovations, Inc., Global Technology Partners, U.S. Defense Dept., Lucent, Yurie Systems, AT&T, Teligent,Inc., Lockheed Missile & Space Systems, C.I.A. Added to these companies are NIAC "advisors" including Lockheed Martin, BellSouth, Symantec, Microsoft, Cisco, Mellon Financial, IBM (ISS), and Pfizer.
These companies all benefitted from the rogue C.I.A.'s installation of strongman Paul Kagame in Rwanda. In exchange for his Central African dictatorship, Kagame has guaranteed them mining access to petroleum, uranium and rare earth minerals used to manufacture products for the computer, mobile phone, TV, defense and high tech industries, as well as bribery and money laundering, including gold, diamonds, coltan, niobium, cobalt and copper in Central Africa.
All of these military-industrial complex companies were beneficiaries of the so-called “Rwanda Genocide” in 1994.
Rwanda
On May 17, 2001, former NSA analyst and Africa specialist, Wayne Madsen, told a Congressional Hearing that the tragic slaughter of one million Rwandans in 1994 was not based on Hutu versus Tutsi tribal hatred run amok.
The genocide narrative had been widely reported by globalists, including Presidents Clinton, Bush, Obama, many in Congress, Wikipedia and the Hollywood film Hotel Rwanda.

Fig. 2—Aerial view of the processing plant at the Tenke Fungurume in 2015 (Congo). Photo: Freeport-McMoRan Copper & Gold.
Rather, Madsen says the Rwandan massacre was a globalist and rogue C.I.A. “false flag” pretext to: (1) depopulate Rwanda and (2) consolidate control of uranium and petroleum as well as rare earth mineral mining of gold, diamonds, coltan, niobium, cobalt and copper in Central Africa.
Madsen and other investigators provide substantial evidence that the Rwandan genocide narrative fails even the most cursory analysis. For example, Wikipedia reinforces the mainstream narrative that 70-80% of all Tutsi Rwandans, representing 800,000 people, were murdered by supposed machete-wielding Hutu killers.
That would put the Tutsi population at 1.1 million. However, only 596,000 Tutsis lived in Rwanda according to the Center for Research on Globalization. Therefore, the globalist narrative is off by almost half. According to eyewitnesses, some mass graves labeled as Tutsi contained just as many Hutu victims.
Tragically, the mass murders in Rwanda were a pretext for the globalist rogue C.I.A. to put Tutsi strongman Paul Kagame into power at any cost to human life.

Fig. 3—
Rwandan Paul Kagame (right). At the time of the October 1990 invasion of Rwanda, Paul Kagame was being trained by the globalist rogue C.I.A. at the Pentagon's General Staff and Command College at Fort Leavenworth, in Kansas (USA). Kagame returned and led the four year war that resulted in the deaths of perhaps several hundred thousand Hutu people between October 1990 and April 1994 alone. From
Keith Harmon Snow. (Apr. 05, 2012). Pentagon Produces Satellite Photos Of 1994 Rwanda Genocide, p. 4.
Conscious Being Alliance.
The rogue C.I.A.’s high technology partners manufacture products and services vital to building a global C.I.A. spy surveillance system that parallels the NSA, but is not subject to the U.S. Constitution. These companies include Sony, Microsoft, Dell, Ericsson, Hewlett-Packard, IBM, Nokia, Intel, Lucent, Lockheed Martin, Boeing and Motorola.
Paul Kagame is a regular guest of Bill & Hillary Clinton, The Clinton Foundation and the World Economic Forum. See “The Global Elite’s Favorite Strongman,” The New York Times, Sep. 07, 2013.
The Clintons' Rwandan racketeering pattern is evident:
- Target the resource that you want to control
- Recruit beneficiaries to this scheme as accomplices
- Infiltrate both the resource holder and his enemies
- Concoct a bad acts pretext to seize control of the resource (sex, drugs, genocide, intolerance, hate, Islamophobia, sexism, homophobia, racism, fake news, The Russians!, whatever works)
- Record your accomplices performing the bad acts to guarantee they don't expose you later
- Plant the bad acts evidence
- Pre-write the media narrative
- Send your mainstream media accomplices the narrative
- Proliferate your fake narrative among your mainstream media accomplices
- Accuse your resource target of your fabricated pretext bad acts
- Press the pretext in the media until you become the holder of the resource
- Or, abandon your pretext if you are exposed or achieve your objective. (e.g., The Russians! pretext was dropped overnight when President Trump bombed Syria)
Kosovo
Stopping genocide was the pretext in Rwanda, we believe.
That worked so well for Clinton that he repeated the playbook in Kosovo.
For the general public at the time, we were told that seething ethnic Serbian-Albian hatred led to "ethnic cleansing!" and "genocide!" in Kosovo. Who could question that story? Most Americans don’t even know where Kosovo is.
Like the rampaging Hutu-Tutsi Rwanda hatred narrative, Serbs and Albanians were characterized as equally seething in Kosovo.
Really? The narrative quickly falls apart upon further investigation.

Fig. 4—Kosovo Refugees.
Why Kosovo? What was the end game?
Only hindsight answers this question: Why Kosovo? Why destabilize Serbia whose Orthodox Christian majority has co-existed with Ottoman Muslims for over 400 years?
Kosovo is a primary migration path for Middle Eastern refugees moving into Europe. Prior to the C.I.A. / NATO intervention in Kosovo, the Balkan borders were guarded by the Serbian government in Bucharest where the predominant religion is Serbian Orthodox Christianity.
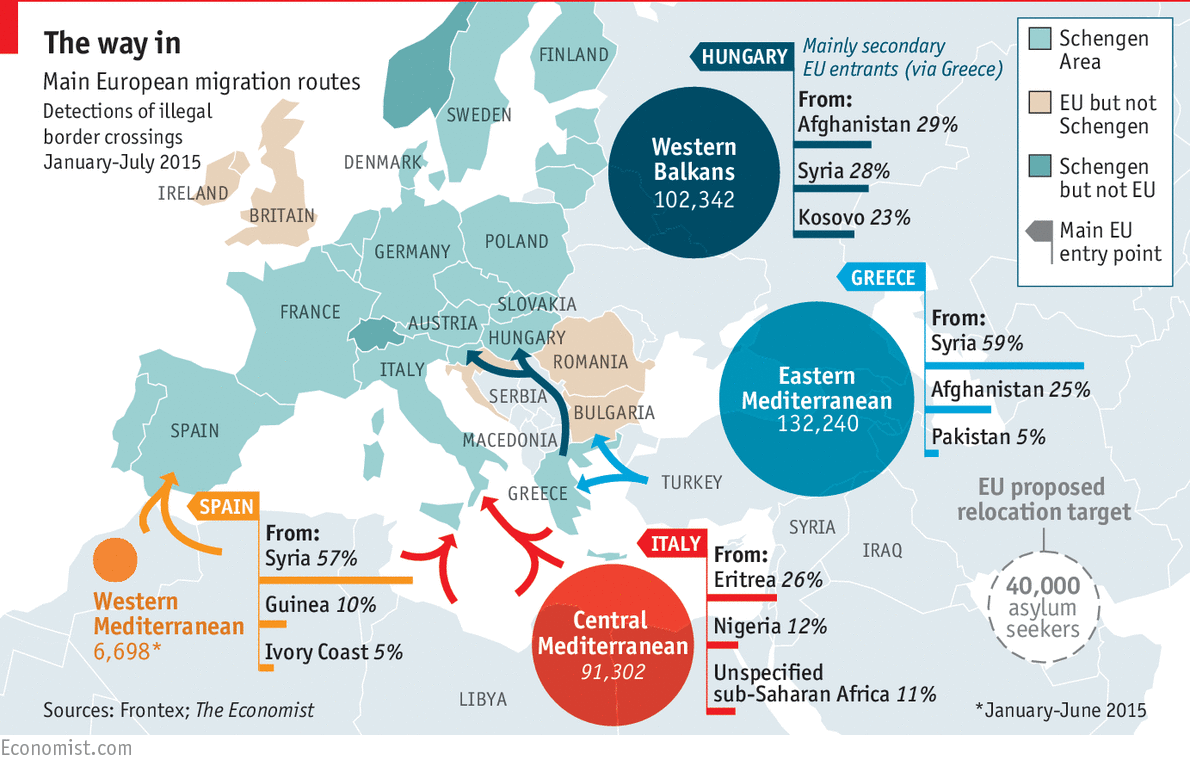
Fig. 5—The way in. Main European migration routes. Detections of illegal border crossings. Jan.-Jul. 2015. The Economist. Graphic:
The Economist.
Serbian Orthodox Christian Church believers reach back to 1st century Apostolic times. Several bishops from the area now called Serbia participated in the First Council of Nicaea (325) where the Nicene Creed was drafted and the Canon of our modern Bible was first compiled. In the history of the Second Millenium, the Serbian Church has thrived despite 400 years of Ottoman Muslim domination (ca. 1459-1879) and 39 years under the Nazis, then Communists (ca. 1941-1980).
Given the choice, Serbian Christians were certain to resist being overrun by the forced migration of Islamists from the Middle East created by ISIS—now proved to be a creation of Hillary Clinton and Barack Obama. Who can fault them for thinking that 400 years of Muslim Ottoman domination was enough? But of course, few in the West knew this history of Ottoman Islamic subjugation of an anciently historic Christian region.
Evidently, the globalists decided that Serbian Orthodox Christians in Kosovo needed to be demonized and Kosovo’s ethnic Albanian Muslim minority given the territory. The Islamist KLA (Kosovo Liberation Army) fighters, including mercenaries from Syria, Yemen, Afghanistan and Saudi Arabia, destroyed 155 Serbian Orthodox Christian churches and monasteries during the conflict, some dating to the 12th century. These are more inconvenient facts proving that the allegations of supposed Serbian genocide were faked.
The amount of human energy, emotion and scholarship that has been consumed to disprove the Clintons' "genocide!" lie is tragic. That time and human creativity could have been so much better spent uplifting humankind rather than having to defend against these devils. Give a devil power and what do you get? Clinton & Co.
As observed earlier, the Clintons learned from Rwanda that genocide sells to an American public that is more concerned about Tom Brady's deflated football and endless titillation from 256-max character text messages.
In seminal testimony to Congress on Feb. 02, 1999, C.I.A. Director George J. Tenet fanned the flames of this narrative when he claimed that the Serbian Army (Christians) had massacred 45 “innocent civilians” in Račak, Kosovo (Muslims).
President Clinton and the mainstream media immediately seized on this story, labeled it genocidal rage, and Račak became the pretext for NATO intervention.
Staged Racak genocidal rage and faked photos

Fig. 6—Račak, Kosovo.
However, investigative journalists for Accuracy in Media discovered that the Račak genocide story was a hoax. They proved that the photos used to justify the NATO intervention were fake. The supposed Račak massacre never happened.
In truth, the French newspaper Le Figaro journalist Christophe Chatelet was in Račak the day of a battle between Serb and KLA forces, just hours after the Serbian forces withdrew.
Chatelet saw nothing notable to an experienced journalist. He saw one dead and four wounded—the casualties of a gun battle between two armies. The next day he returned with colleague Renaud Girards to an international media circus with 45 civilian bodies staged in the streets and farmhouses. He saw perhaps a dozen or more bodies thrown into a ditch that weren't there the day before. And, he did not see the commensurate spent bullet shell casings that one would expect at the scene of a mass murder of civilians at close range (Clinton's speech:"sprayed with bullets"). Nevertheless, newly-minted talk of Serbian Army genocide was repeated in unison by the KLA fighters who had returned after the battle. Clearly, Račak was chosen as Clinton's pretext for NATO/U.N. intervention.
President Clinton jumped on the fabricated genocide narrative and painted a horrifying picture of Serbian (Christian) atrocities against the KLA (Islamists), saying:
"We've seen innocent people taken from their homes, forced to kneel in the dirt and sprayed with bullets; Kosovar men dragged from their families, fathers and sons together, lined up and shot in cold blood. This is not war in the traditional sense. It is an attack by tanks and artillery on a largely defenseless people whose leaders have already agreed to peace." Clinton declared, "Ending this tragedy is a moral imperative."
The New York Times chimed in, saying:
"Some of the dead were found with their eyes gouged out or heads smashed in, and one man lay decapitated in the courtyard of his compound. The victims included one young woman and a 12-year-old boy. Many were older men, including one who was 70." It added that "many had been shot at close range" and that villagers said that "the Serbian forces had rounded up the men, driven them up the hill and shot them." Amb. William Walker, head of the Kosovo Verification Mission, had called this an "unspeakable atrocity" and "a crime against humanity."
Notice the Extreme Emotion Baiting by President Clinton and The New York Times—"forced to kneel in the dirt" "sprayed with bullets" "dragged from their families" "lined up and shot in cold blood" "defenseless" "eyes gouged out" "heads smashed in" "decapitated" "13-year old" "older men, one 70" "shot at close range" "rounded up" "unspeakable atrocity" "crime against humanity"
These are mass media emotion triggers
developed and tested by the C.I.A.'s MKUltra mass mind-control program. These smear techniques were used succesfully by Hillary Clinton against Donald Trump. Fortunately, not used well enough. Perhaps America's lethargic public is finally waking up?
When Le Figaro's Christophe Chatelet was asked how he could explain how his report the previous evening of one dead could have ballooned to 45 bodies strewn all over the village and talk of genocide. He said, "I can't solve that mystery."
Despite the Le Figaro journalists confirming that Račak was a hoax, members of Congress quickly fell in line behind the Islamist KLA (Kosovo Liberation Army). They even compared the KLA to America’s 1776 colonist “freedom fighters.” No one seemed to care that many of the KLA fighters were imported from Yemen, Syria, Afghanistan and Saudi Arabia.
“genocide!” a pretext that has worked ... no more
The “genocide” narrative has worked. Rwanda and Central Africa are today controlled by a C.I.A.-installed strongman. Central Africa's rare earth minerals and blood diamonds flow freely to America's rogue C.I.A. and its high technology military-industrial complex. Rwandans mourn their dead souls.
An Islamist-controlled Kosovo has allowed the free flow of Syrian immigrants into Western Europe. Kosovars mourn their dead souls.
Clearly, accusations of genocide are easily sold as pretexts to a sleeping, undiscerning public. What was not fake was the tragic murder of over a millions of Rwandans and Kosavars. Did the parents of these globalists not teach them that mortality and judgment for our deeds before God comes to us all?
Bill Clinton oversaw two “genocides” in small countries during his eight years in office. Both pretexts saw minorities aligned with the globalist rogue C.I.A. come to power.
In true Saul Alinsky form (accuse your opponent with what you are doing), the victims in Rwanda and Kosovo were called the butchers.
What is different now?
- The Clintons are out of power
- George Soros no longer runs the U.S. State Department
- The Clinton Foundation is exposed
- The Deep State shadow government has been exposed
- A rogue C.I.A. is exposed
- The British have voted to leave the European Union
- Donald Trump is President
- Populism over globalism is exploding worldwide
Defeat the Globalists
Justice for their victims
The rogue C.I.A. globalist shadow government is currently in control of global Internet “Big Data” and is spying on all of us.
Bill Clinton, George Bush and Barack Obama enabled a C.I.A.-run shadow government to be established that controls our technology led by IBM, Microsoft, Google, AT&T, Cisco, Yahoo, Oracle, EMC, Dell, Lenovo, Symantec, Juniper and Facebook, among others.
This rogue C.I.A. technocracy is running the Internet and must be dismantled.
"The Internet of Things" Silicon chips have rogue C.I.A. backdoor keys burned on them
WikiLeaks, Shadow Brokers and others have shown us that the current Internet is fundamentally compromised down to the electronic chip level and must be scrapped.
No amount of adjustment can fix a silicon chip with a backdoor encryption key burned onto the circuitry. That chip must be thrown away.
This is the devilish level to which the rogue C.I.A. has stooped to accomplish its technocratic takeover. They appear hell bent on robbing our property, privacy and well-being to control us forever.
We need a digital Manhattan Project to fix the Internet. Now.
* * *
Notice: This post may contain opinion. As with all opinion, it should not be relied upon without independent verification. Think for yourself. Photos used are for educational purposes only and were obtained from public sources. No claims whatsoever are made to any photo. Fair Use is relied upon.
Comment
Click "N comments:" on the line just below this instruction to view comment on this post. On about Dec. 05, 2016, Google began blocking comments to this blog. However, if you email your comment to a secure email website we have established at:: afi@leader.com we'll post it for you. We welcome and encourage anonymous comments, especially from whisteblowers.


 e.g. "IBM Eclipse Foundation" or "racketeering"
e.g. "IBM Eclipse Foundation" or "racketeering"